Cross-Site ETag Length Leak
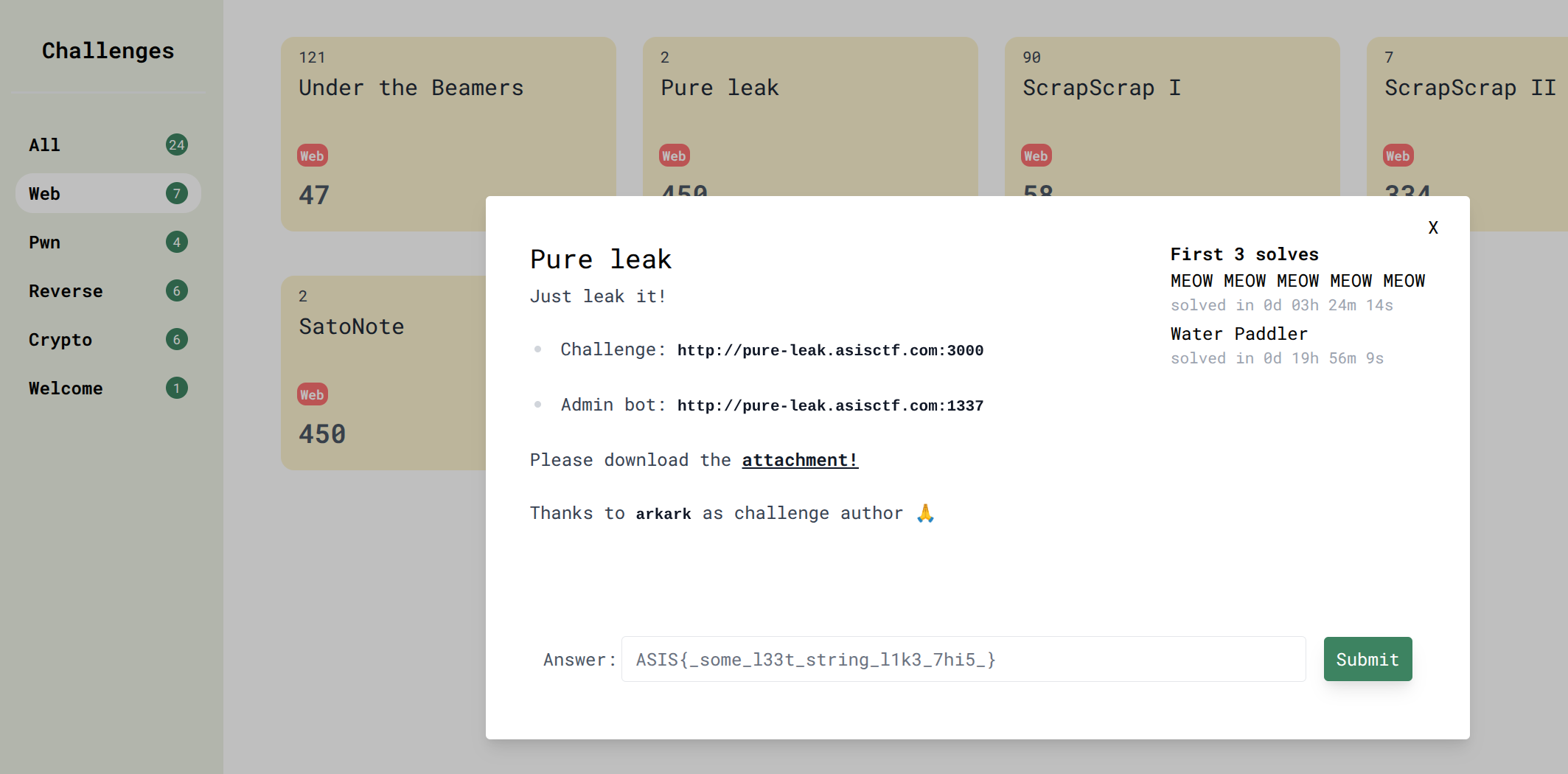
I recently discovered a new client-side attack technique that leaks the length of an ETag from a cross-site page. This can be used as an XS-Leak oracle and I created a CTF challenge as a proof of concept.
impossible-leak is one of the challenges I authored for SECCON CTF 14 Quals1:
- Difficulty: 1 solve2 / 500 pts
- Author: me
- Source: https://github.com/arkark/my-ctf-challenges/tree/main/challenges/202512_SECCON_CTF_14_Quals/web/impossible-leak
This technique is likely applicable beyond this specific challenge. We can use it as an unintended solution in other XS-Leak challenges. In fact, I first came up with it as an unintended approach during an earlier CTF and later refined it into a standalone technique.